Panzura has added Access Control List (ACL) analysis and automated remediation to the Symphony data management offering.
Symphony software, positioned as a data services platform, discovers and manages exabyte-scale unstructured – file and object – datasets, with scanning, tiering, migration, risk, and compliance analysis features. It complements Panzura’s CloudFS hybrid cloud file services offering. Panzura claims that 58 percent of enterprises are affected by an epidemic of permissions sprawl and 74 percent of data breaches involve privileged credential abuse.

Panzura CTO Sundar Kanthadai states: “Manual permission audits are a nightmare – teams are constantly chasing inheritance chains, investigating anomalies, and trying to resolve violations. Automated ACL remediation is the difference between damage control and strategic access governance, a capability often promised but never delivered with such precision.”
According to Panzura, 91 percent of employees still have access to company files after offboarding. It claims that “the average cost per insider incident has reached $16.2 million, driven by permission failures including lack of centralized management, limited access control, excessive privileges, unrevoked access, shared credentials, organizational growth including M&A and restructuring, and third party access.”
It says that managing file permissions – including Discretionary Access Control Lists (DACLs) and System Access Control Lists (SACLs) – has become a challenge for IT administrators and security teams. The core problems are orphaned files from deleted users, overly permissive ACLs, broken inheritance, and shadow IT. These issues create security risks, trigger compliance violations, and undermine operational efficiency.
This latest Symphony release focuses on problems like broken permission inheritance, over-privileged access, and compliance blind spots. It adds new metadata across the entire data environment, including ownership and comprehensive ACLs, that can later be interpreted.
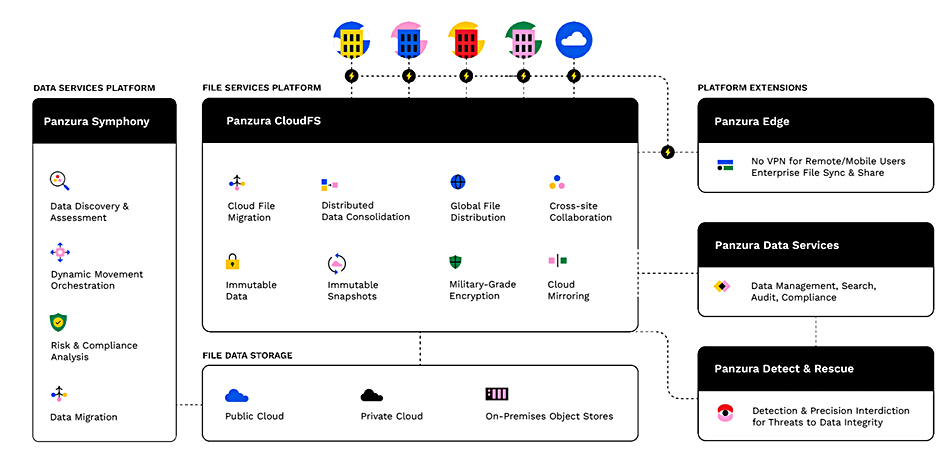
Symphony identifies and remediates anomalous permissions across entire file system estates regardless of the underlying infrastructure, providing full visibility into who can access what and enabling fast resolution of problematic access. It enables automated detection and mass permission changes and has the ability to apply custom metadata to files, enabling advanced policy automation, and fueling AI pipelines based on file attributes without content scanning. Support has been extended to Windows Alternate Data Streams (ADS) and Extended Attributes (EA) for greater visibility and automation.
It “provides actionable metadata insights, automating data movement between file systems, object stores, and cloud storage for petabyte-scale data orchestration, storage cost optimization, and AI workload placement.”
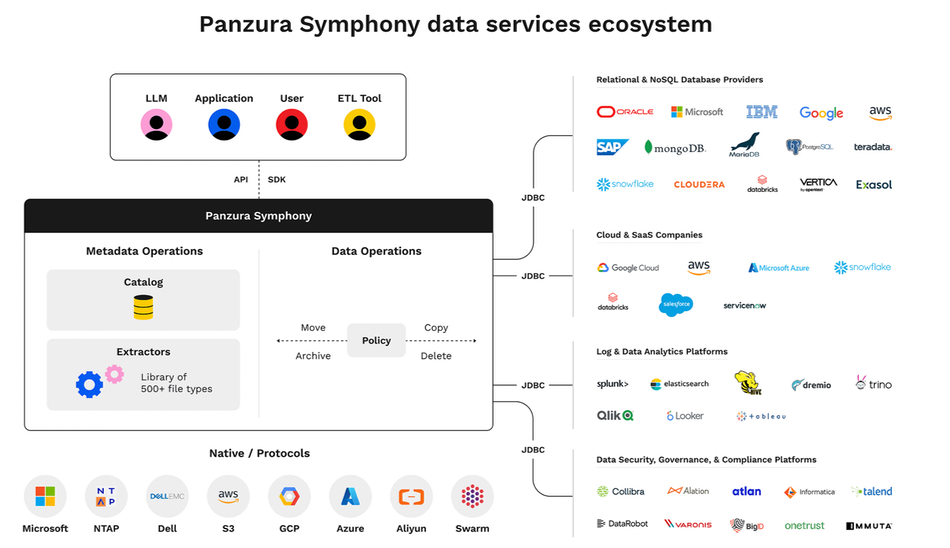
Admins can access the platform through the Symphony AdminCenter – a centralized web-based interface for policy management, task scheduling, server monitoring, and file reporting. Alternatively, integration is straightforward with comprehensive REST API, JDBC database support, and webhooks for seamless DevOps workflows. It also enables enterprises to crawl their systems, tag their data, report on the veracity of potential large language model (LLM) data, and offer categorized data for specific enterprise functions.
According to Panzura, Symphony orchestrates and optimizes file and object data across any infrastructure while ensuring data quality, accessibility, and proper categorization, delivering proactive security and compliance with clean, well-governed data.
Kanthadai said: “Security through obscurity is no longer an option. The latest capabilities of Symphony specifically address the daily challenges sysadmins face in maintaining secure and compliant data storage and preparing data for AI workloads including agentic AI.”
Symphony is immediately available to existing customers for both Enterprise and Insights editions of the platform through standard updates and to new customers through direct sales and Panzura’s global partner network. Read a product brief here.
Bootnote
Interactive ACL Analysis in Symphony enables administrators to identify exactly where permissions change in the directory tree. This capability provides:
- Clear, drill-down views of complex permission inheritance
- Human-readable DACLs and SACLs with adjustable detail levels
- Change tracking from previous scans to spot potential suspicious activity
- Export to database, CSV, or JSON for further analysis
Symphony can automatically remediate ACL anomalies with the Repair ACLs Policy. The system analyzes and repairs broken ACL inheritance for both DACLs and SACLs automatically using administrator-defined policies. Panzura says: “Proactive remediation is a crucial differentiator for Symphony, moving beyond visibility to actual problem resolution that other solutions lack.”
Advanced metadata management provides:
- Dataset selection based on metadata presence or content
- Comprehensive EA reporting in Scan Policies
- Export to database, CSV, and JSON formats
- Set or remove EAs
- Set EA values directly from database and catalog sources
Panzura Symphony now has support for NetApp FlexGroup Volumes and includes support for IBM Storage Deep Archive for cold data, enabling on-premises archiving of massive datasets using an S3 Glacier compatible interface.
Competitor Komprise added automated destination share and user/permission mapping in its latest Elastic Data Migration release, with a security identifier (SID) mapping, automating the process of changing owner and group permissions when migrating files based on customer-defined mapping policies.
Datadobi’s StorageMAP ensures that file and object permissions, including ACLs and metadata (e.g. ownership, timestamps), are preserved during migrations across heterogeneous storage systems, such as NFS, SMB, and S3-compatible platforms. Its tagging capabilities allow administrators to assign attributes like ownership, sensitivity, or required actions to data. These tags can be used to enforce permissions policies, such as restricting access to certain users or groups or flagging data for compliance reviews.








