Just over half of enterprises with more than 10,000 employees have integrated storage security into their overall cybersecurity strategy, with another fifth planning to do so.
The finding was revealed by an Infinidat-sponsored survey by The Register and Blocks & Files that looked at cyber strategies for data infrastructure protection, priorities, and buying patterns of CISOs, CIOs, and VPs of IT Infrastructure of such large enterprises.

Infinidat CMO Eric Hezog stated: “Being able to recover business-critical and mission-critical data as fast as possible after a cyberattack, such as ransomware or malware, is an organization’s last line of defense. Any enterprise that does not deploy cyber resilient storage leaves themselves at high risk and defenseless.”
In the surveyed organizations, CISOs were the main drivers for cybersecurity (55.6 percent), with CIOs next (27.5 percent), and few relying on a VP of infrastructure (7.5 percent), chief legal officer (6.2 percent), and VP or director of storage (3.1 percent).
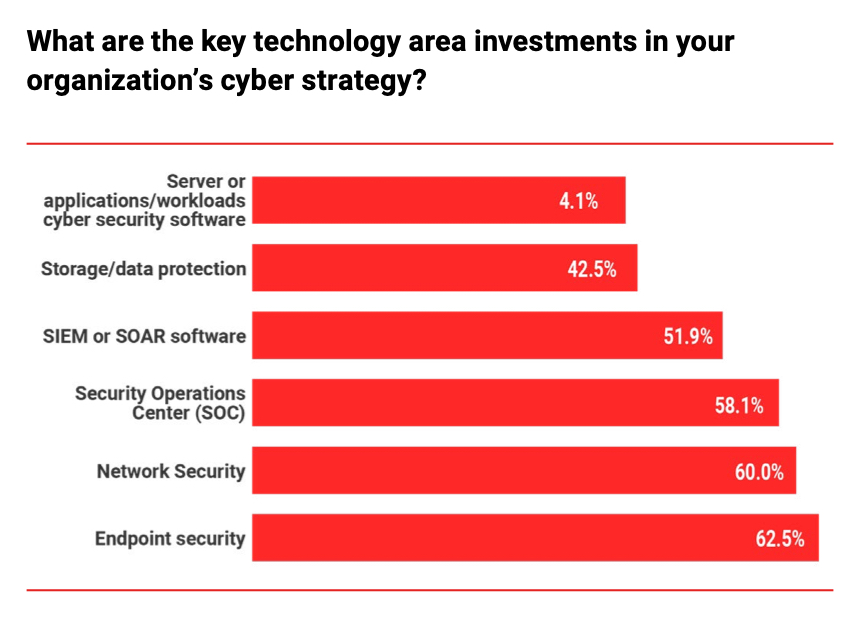
Cyber strategy investment areas followed an outside-in and overlapping pattern, with endpoint security first (62.5 percent), network security (60 percent) next, and a security operations center third (58.1 percent). SIEM or SOAR software was fourth at 51.9 percent, then storage and data protection came in at 42.5 percent. Just 4.1 percent looked at server or app workloads and cybersecurity software as a key technology investment area.
Unsurprisingly, only 13.1 percent of respondents thought it unimportant to have automated detection and recovery processes. 30 percent said it was mandatory, 30 percent said very important, and 26.9 percent said somewhat important.
A majority of respondents (56.2 percent) took the view that storage security information, such as logged events, should be integrated into the overall security environment. Only 17.5 percent of respondents took the view that such integration was not necessary, with a further 6.9 percent having no integration plans. Partial integration was being undertaken by 15 percent, while 4.4 percent were planning such integration in the future.
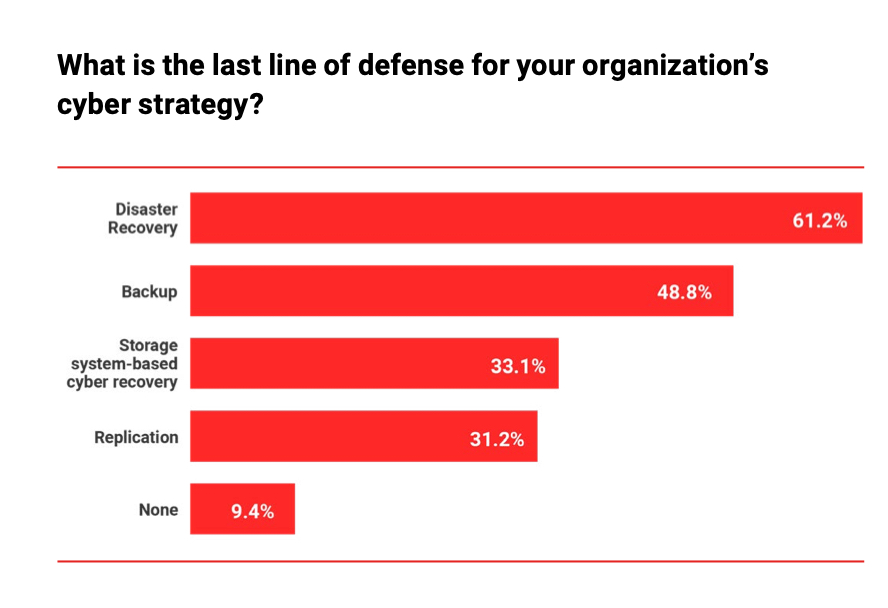
When asked about their last line of cybersecurity defense, multiple options were mention. Most respondents (61.2 percent) answered disaster recovery, 48.8 percent said backup, 33.1 percent said cyber recovery was storage system-based, and 31.2 percent said it was replication. A minority (9.4 percent) said they had no last line at all.
The distribution of recovery SLAs was surprisingly variable:
- <30 minutes – 21.2 percent
- 30-60 minutes – 10.6 percent
- 1-12 hours – 30 percent
- 24 hours – 16.2 percent
- 1-10 days – 21.9 percent
Infinidat says its cyber recovery guarantee for InfiniBox and InfiniBox SSA – one minute or less, regardless of dataset size – meets the fastest recovery SLA listed.
Finally, there were multiple ways to verify restored data to ensure it was fully present and malware-free. Application owners had the most responsibility (50.6 percent), followed by vendor-supplied backup or storage tools (47.5 percent), then security/forensic consultants (40 percent), and tools from security vendors (37.5 percent).
The survey report notes: “Keeping critical data and applications safe from threats is a constant battle for every organization, and orchestrating and validating a fast recovery in the event of any incident is an equally important element of any effective cybersecurity defense.”
Enterprise storage vendor Infinidat has hardened its product line with InfiniSafe offerings to help keep its users safe from cyberattacks. InfiniSafe Cyber Detection provides AI and ML-based deep scanning and indexing of the stored data estate to identify potential issues and help enterprises react, resist, and quickly recover from cyberattacks.
InfiniSafe Automated Cyber Protection (ACP) integrates with an enterprise’s security operations center (SOC) and/or their datacenter-wide cybersecurity software applications.
Herzog believes that there is “a shift happening in the enterprise market toward embracing a cyber-focused, recovery-first approach to mitigate the impact of cyberattacks.” First stop the attack, then aim to identify and recover the affected data, followed by forensic analysis and procedural changes to IT systems and processes. Such changes should include integrating automated cyber protection, accelerating cyber detection, and incorporating cyber storage resilience and rapid recovery into an enterprise’s overall cybersecurity strategy if that hasn’t already been done. The increasing incidence and scope of malware attacks shows no sign of slowing down.
Malware resistance and recovery require constant vigilance by every employee against phishing attacks, for example, and the provision of cyber-resilience for storage and the data estate integrated into the organization’s overall cybersecurity arrangements. Inadequate storage array security is an open door to malware miscreants.
You can read the survey report here.